Code Quality & Architecture Assessment
Evaluate your codebase structure, design patterns, maintainability, and technical debt.
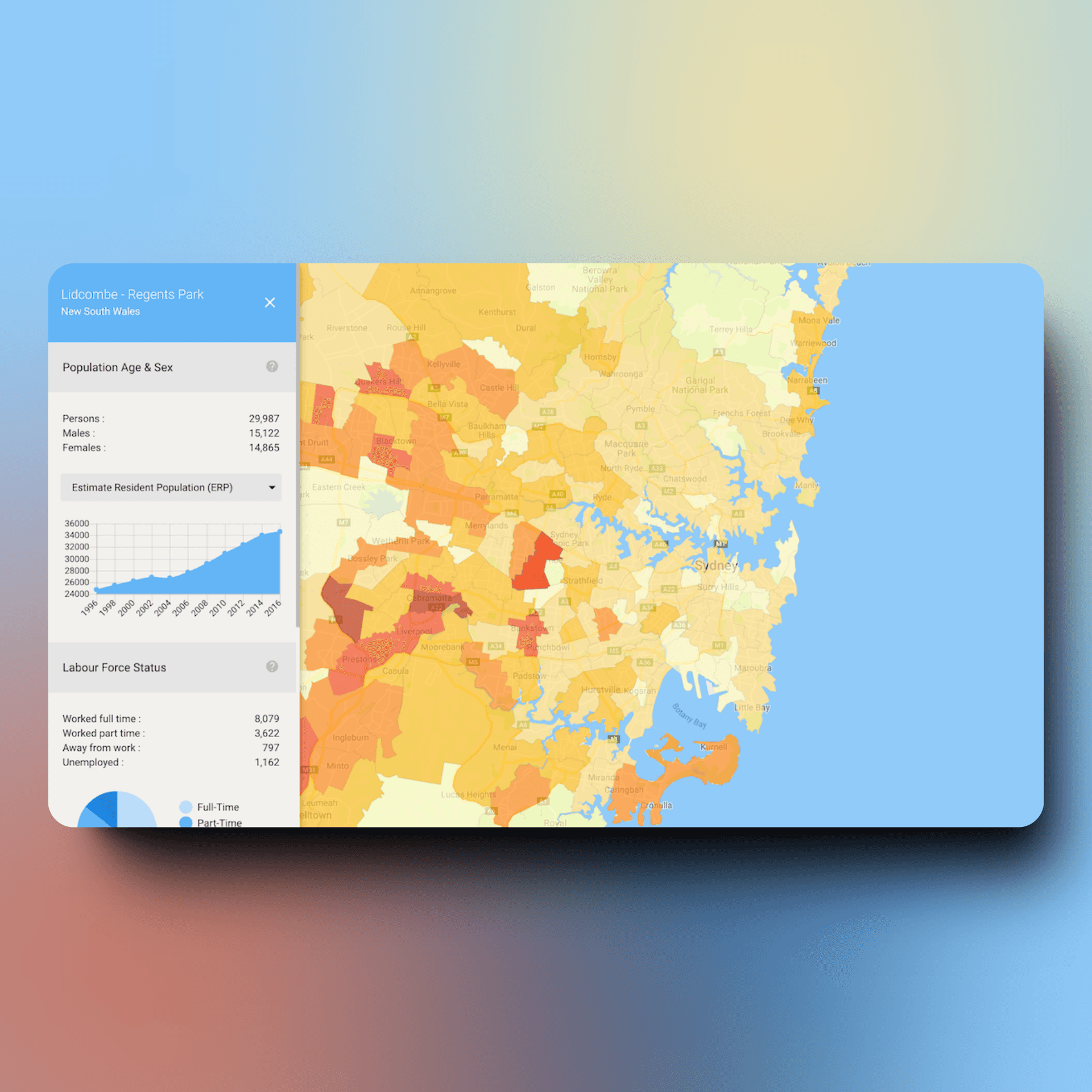
- Architecture review assessing modularity, scalability, and adherence to best practices
- Code quality metrics including complexity, duplication, maintainability index, and test coverage
- Design pattern analysis identifying anti-patterns and opportunities for refactoring
- Dependency audit evaluating third-party libraries for security, maintenance status, and licensing